Healthcare Database Breaches
The healthcare sector has seen a digital change following the Internet of Medical Things, smart devices, information systems, and cloud services. Lives remain now much more pleasant due to the advancements in digital healthcare services. More so, which have simplified treatment and made it more accessible. However, internal and external attacks have made the modern healthcare sector the main victim (She et al., 2020). Data breaches affect customers, stakeholders, organizations, and enterprises and challenge security specialists (Healthcare Database Breaches).
Healthcare Database Breaches
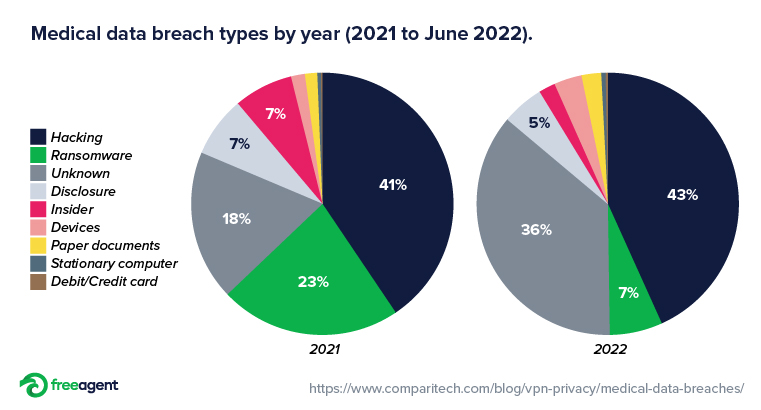
Despite the variety of data breaches, they virtually always have the same effect. Unauthorized individuals occasionally access healthcare databases due to software flaws, security lapses, and human error. As a result, sensitive data remain exposed through data breaches. Sensitive healthcare data may occasionally remain lost, stolen, or disclosed. Moreover, due to insider attacks that harm protected health information (She et al., 2020). On the dark web, a full record file for a single patient can cost hundreds of dollars. The healthcare sector remain among those most negatively impacted compared to other data industries.
Poor organization security leads to the compromise of most health records. The average number of records impacted by a breach brought on by inadvertent insider threats remain more than twice as high as that of breaches brought on by theft and other malice, such as foreign cyberattacks. In a study, breaches caused by inadvertent factors accounted for 73.1 percent of all affected records. Consequently, malicious factors were responsible for 26.7 percent (Yeo & Banfield, 2022) (Healthcare Database Breaches).
Carelessness and negligence (382 instances) are the most prevalent causes of cyber breaches in HCOs, ahead of theft (222 instances) and phishing attacks (221 instances). 212 (55.5%) of the 382 occurrences involving carelessness or ignorance involved employees or business partners sending PHI to unauthorized people through mail or email (Yeo & Banfield, 2022). Some resulted from incorrect printing alignment or information incompatible with patient information (Healthcare Database Breaches).
Other times, PHI might have been sent to the right people by mail. However, it may have done so in a way that unintentionally exposed the PHI while it was being delivered. In 71 occurrences, lost hard drives or papers containing PHI in the mail or during transit were mentioned (Yeo & Banfield, 2022). Conclusively, human errors are significant sources of data breaches in an organization (Healthcare Database Breaches).
Cyber risk assessments and security evaluations should be carried out yearly to address these problems and resolve any new vulnerabilities, security holes, or out-of-date policies that may put the organization in danger. HIPAA rules can guide organizations looking to enhance data privacy (Chin, 2023). Network segmentation remain a highly effective data security method that uses split subnetworks.More so, to restrict data access across an organization’s computer network, especially in larger businesses or hospitals.
However, every business, from small service providers to large hospitals, must offer sufficient cybersecurity training so employees can act as the first line of defense against attacks (Chin, 2023). Healthcare businesses should teach new hires about cybersecurity and remind relevant personnel with access to sensitive data about optimal data protection procedures (Healthcare Database Breaches).
References
Chin, K. (2023, April 5). How the healthcare industry can prevent data breaches. Third-Party Risk and Attack Surface Management Software | UpGuard. https://www.upguard.com/healthcare-prevent-data-breaches
Seh, A. H., Zarour, M., Alenezi, M., Sarkar, A. K., Agrawal, A., Kumar, R., & Khan, R. A. (2020). Healthcare Data Breaches: Insights and Implications. Healthcare (Basel, Switzerland), 8(2), 133. https://doi.org/10.3390/healthcare8020133
Yeo, L. H., & Banfield, J. (2022). Human Factors in Electronic Health Records Cybersecurity Breach: An Exploratory Analysis. Perspectives in health information management, 19(Spring), 1i.
